Security FAQ
Updated June 2024
What Is Convertr?
Convertr an API-first data routing and optimization platform. We capture marketing lead information from multiple sources (landing page forms, imports, API requests, and webhooks) and verify, validate and enrich the data before routing the data into a client's marketing system, usually a CRM system.
Convertr is a SaaS platform that is licensed by our direct client. We provide all the tools to improve data security by automating manual processes and reducing the risk of data being mishandled.
How is your internal network secured?
What other protection methods does Convertr have in place?
Can you provide an audit trail?
Does Convertr have any certifications?
What is the Convertr platform uptime?
What assurance documentation can you provide?
Does Convertr have a business continuity plan?
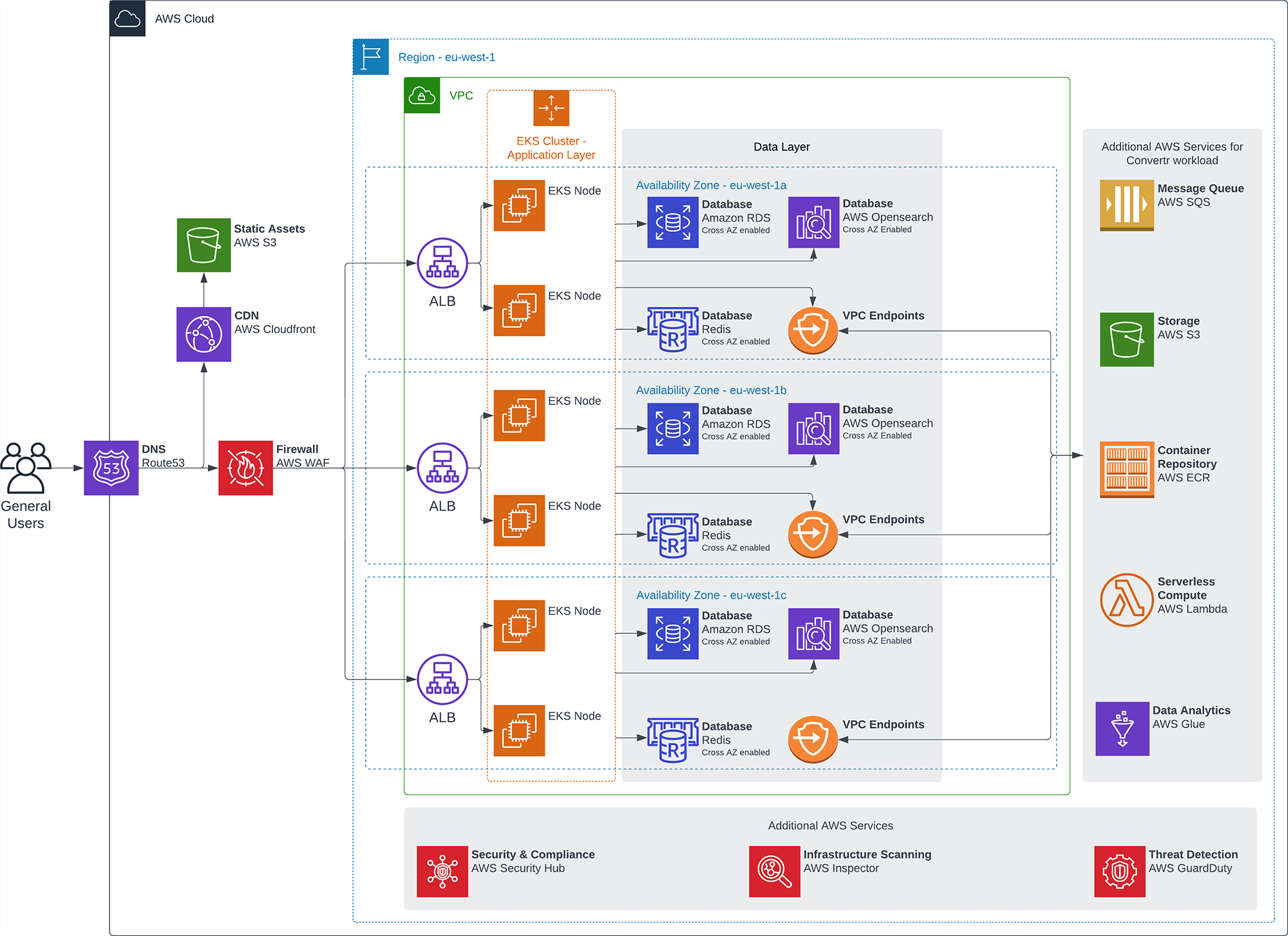
What does the Convertr infrastructure look like?
Controls Summary
How is data stored and secured in the Convertr platform?
The security of our clients’ data is our number one priority. Convertr is fully hosted on AWS (Amazon Web Services) enabling us to leverage their state of the art physical and virtual security. You can read more about AWS’ security measures here.
All data transferred is secured by TLS 1.2.
Location
Our default location for data storage is in Ireland, but can be hosted in any AWS region if required (additional costs may apply). The cluster is limited to this area and no data will flow outside of this region without explicit consent from the client.
Encryption
We encrypt all personal data at rest in the database using AES256 encryption with rotating keys. In addition, each client has its own private database with unique application access. Convertr also uses disk encryption for all AWS services.